Difference between revisions of "Log in"
| Line 24: | Line 24: | ||
* Limit incoming requests for all Administrator functionality to a static IP range | * Limit incoming requests for all Administrator functionality to a static IP range | ||
| − | By default, these settings are turned off, and must be turned on by an administrator in Administer > Settings > Security. For more information on using these new login security features, please see the [ | + | By default, these settings are turned off, and must be turned on by an administrator in Administer > Settings > Security. For more information on using these new login security features, please see the [https://www.ica-atom.org/doc/Settings Administer > Settings] page of the User Manual. |
[[Category:User manual]] | [[Category:User manual]] | ||
Revision as of 18:05, 22 August 2012
Please note that ICA-AtoM is no longer actively supported by Artefactual Systems.
Visit https://www.accesstomemory.org for information about AtoM, the currently supported version.
Main Page > User manual > Getting started > Log in
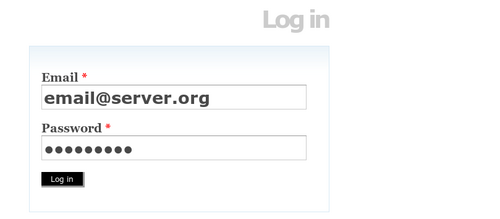
To add or edit content in ICA-AtoM, you need to log in:
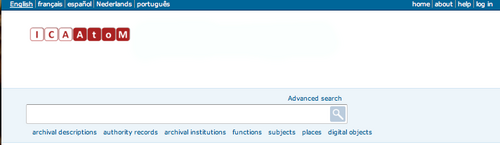
- Click the log in link in the user menu in the upper right-hand corner of the page. ICA-AtoM routes you to the log in page
Enter your email address
- Enter your password
- Click the log in button
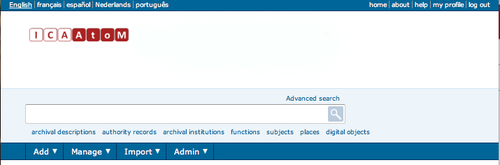
ICA-AtoM re-loads the home page, now customized to your user role. The main menu is now visible.
- To log out, click the log out link in the user menu, ICA-AtoM returns you to the home page (view-only access)
- Note that ICA-AtoM automatically logs you out after thirty minutes of inactivity. To resume editing, you will have to log back in
New Login Security Features in ICA-AtoM 1.3!
If you are running the latest release of ICA-AtoM (version 1.3, available here), administrators now have the option to:
- enhance the security requirements for user passwords, to ensure they are strong.
- enhance the login process to force all authenticated user requests to https for more secure network communication (requires the user to have an SSL certificate)
- Limit incoming requests for all Administrator functionality to a static IP range
By default, these settings are turned off, and must be turned on by an administrator in Administer > Settings > Security. For more information on using these new login security features, please see the Administer > Settings page of the User Manual.